22.06.2017
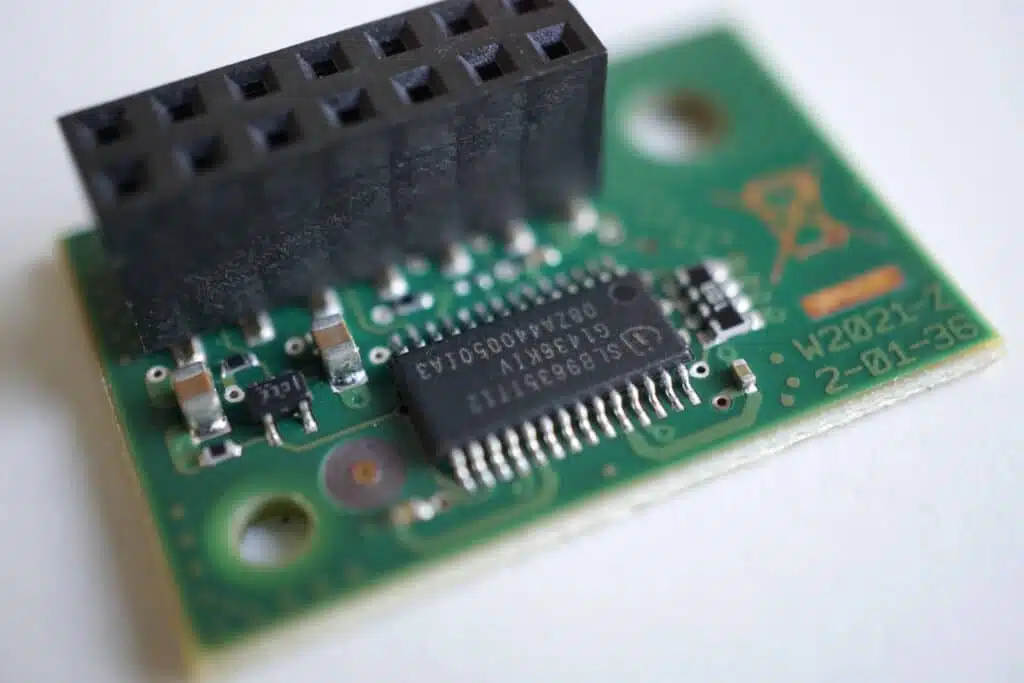
The Trusted Platform Module (TPM) is a chip that is integrated in many systems and offers more security. It is mainly used in PCs, notebooks and cell phones, but also in consumer electronics. A device with TPM, a customized operating system and suitable software is referred to as a Trusted Computing Platform (abbreviated to TC platform).
The advantages of the TPM lie in the security and encryption as well as the identification of devices. Each chip contains a unique cryptographic key that can be used to identify the computer, provided the owner allows it to be read.
Cryptographic keys can also be stored in the TPM to store encrypted data outside the TPM. The keys are generated, used and securely stored within the TPM so that they are protected against software attacks. Other advantages include better license and data protection. The owner of the system can sign data to prove his authorship. The TPM can also be used to detect changes made to the system, e.g. by malware or users.
The endorsement key (EK) is an RSA key pair (the abbreviation RSA stands for the three mathematicians Rivest, Shamier and Adleman, who developed this cryptographic procedure) and is uniquely assigned to each TPM. The key length is 2048 bits. The RSA key pair consists of a private key for decrypting or signing data, which must never leave the TPM, and a public key for encryption and signature verification. The key can be generated outside the TPM and can also be deleted and regenerated.
The Storage Root Key (SRK) is created when an admin or user takes over the system, i.e. when the owner of the computer changes. The SRK is also an RSA key with a length of 2048 bits. As the name suggests, it is the root of the TPM key tree, as it encrypts other keys used.
The Attestation Identity Keys (AIKs) are also RSA keys with a length of 2048 bits. They are created using the endorsement key and protect the user's privacy. The AIKs are effectively a pseudonym for the EC so that it can remain anonymous.
The decisive factor for the use of TPM is, of course, a TPM chip integrated into the hardware. This is sometimes located on the mainboard by default, but the module can often be installed as an option if a TPM header is available. However, the right software is also required to use TPM. A secure operating system, such as Windows 10 IoT Enterprise , is recommended so that the software cannot be manipulated so easily.
A TPM chip is integrated in the spo-comm systems spo-book WINDBOX III Advanced, spo-book NOVA CUBE Q87 and spo-book BOX N2930 (TPM 1.2 in each case). The successor to the spo-book WINDBOX III Advanced will be released in the third quarter of 2017 and will include the new TPM 2.0 standard published in 2014. TPM can also be optionally installed in the spo-book TURO Q87, spo-book EXPANDED Q170 and spo-book NINETEEN Q170 systems.

Last month, we were at Embedded World and gained many valuable impressions. In addition, our ONE H61...
Mini PCs are playing an increasingly important role in today's industry - whether in manufacturing, ...

At the start of the new year, we also have news to announce from the spo-comm ranks. The NINETEEN is...
Otto-Kraus-Straße 4c
D-90411 Nuremberg
Phone: +49 (0) 911 / 23 98 37 – 0
E-mail: info@spo-comm.de
You need to load content from reCAPTCHA to submit the form. Please note that doing so will share data with third-party providers.
More Information