28.03.2017


Edge AI is the combination of artificial intelligence and local data processing directly at the poin...

This was our start to the new year: the current memory and CPU situation continues to have a major i...
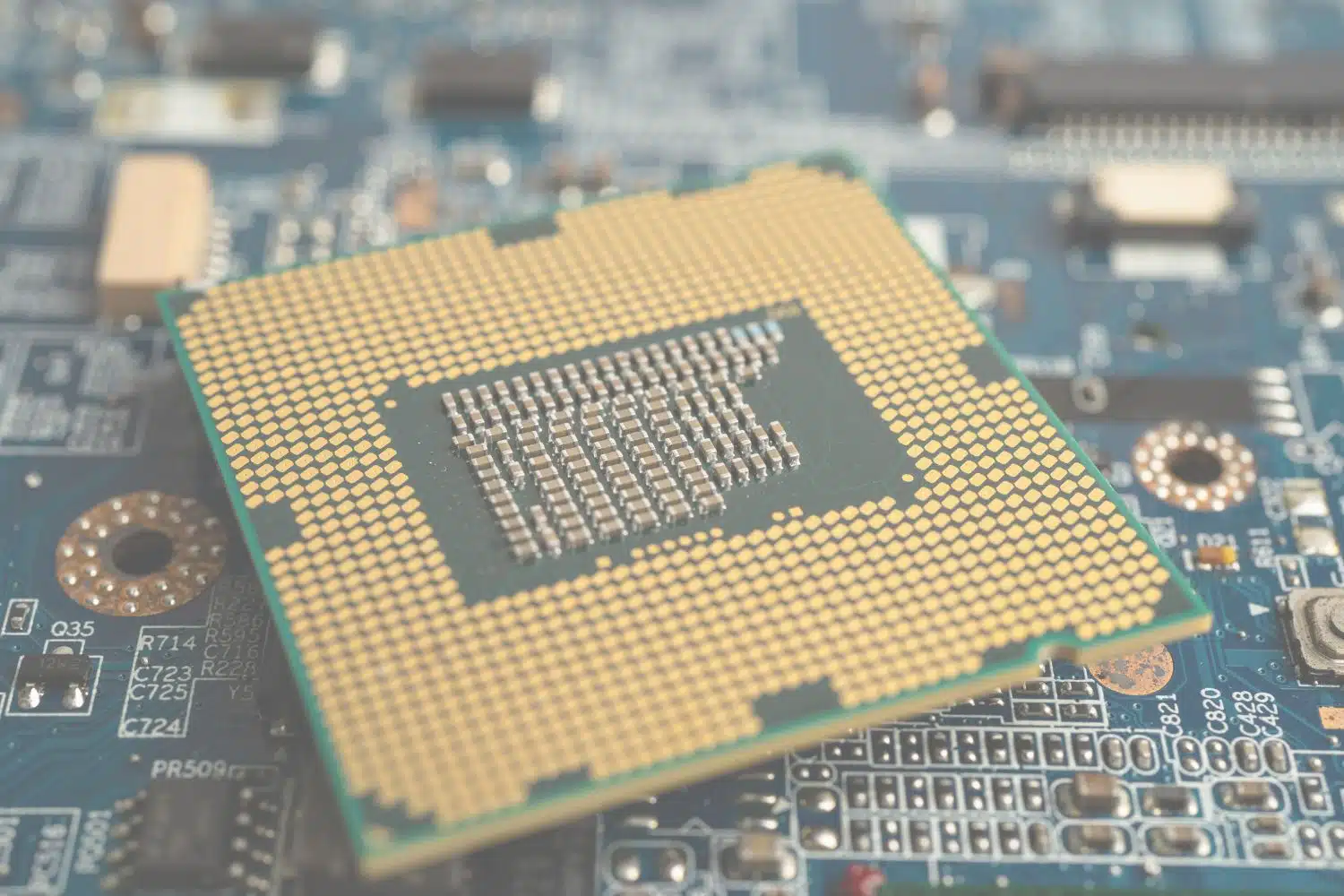
There is currently a global crisis in the areas of RAM bars and CPUs. What began last summer as a mo...
You need to load content from reCAPTCHA to submit the form. Please note that doing so will share data with third-party providers.
More Information